constellation
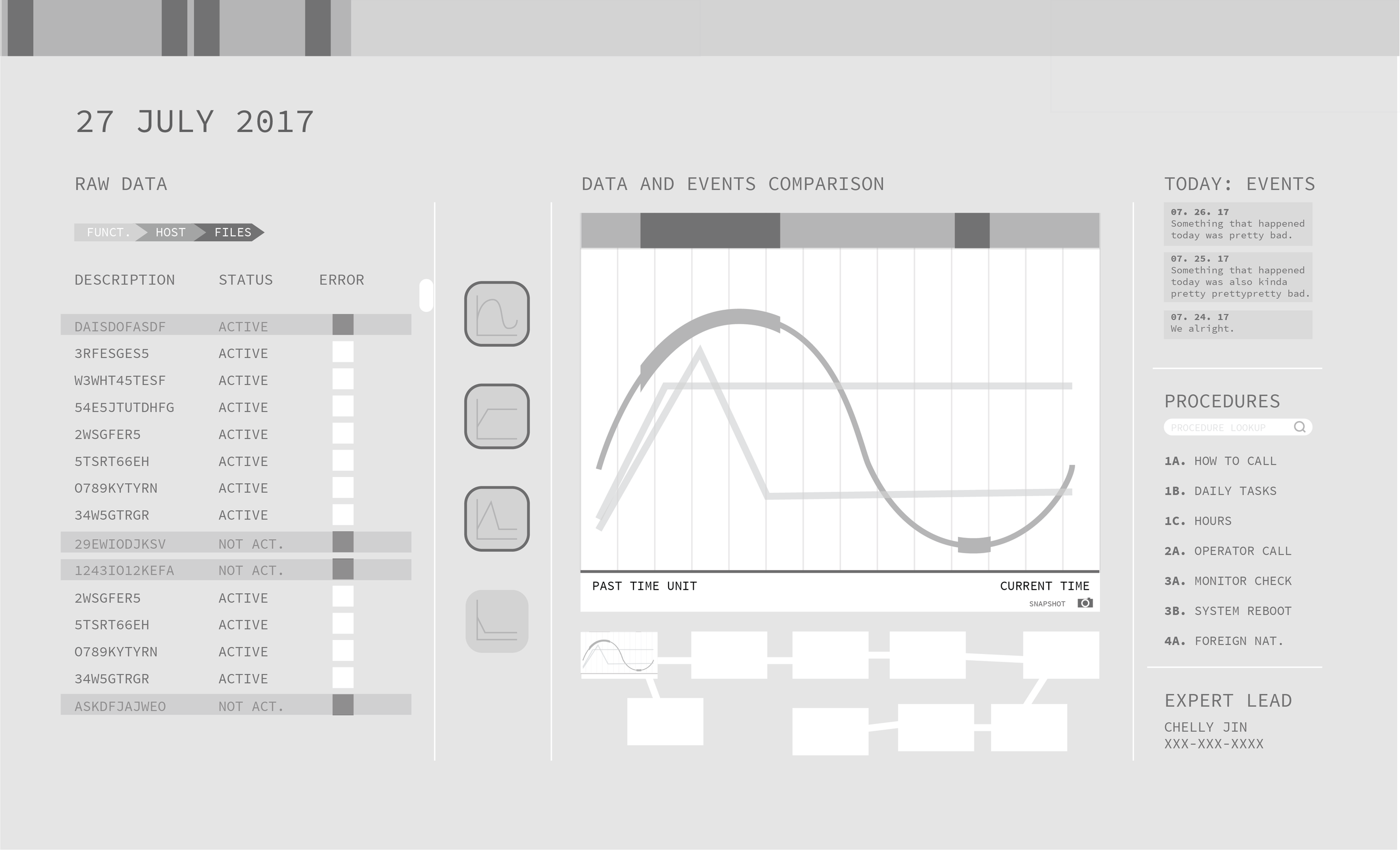
Cybersecurity analysis system for NASA Jet Propulsion Lab's cybersecurity team, CDER. Constellation visualizes anomalies in the Mars Science Laboratory's (MSL) ground support system (GDS) health with a real-time display that provides situational awareness of the entire system state while being actionable.
Overview Breakdown
Every spoke within a circle represents a computer.
Every circle represents a group of computers (within a room or a specified location).
Every concentric circle is a 15 minute increment over a one hour timeline.
Every white dot that appears is an anomaly, scaled to the strength of the anomalous activity.
Main Design Decisions
Consistent colors make it easier for analysts to quickly pick out problems (ie. white indicates issue, while darker purples subside into the background).
Ambiance and calmness are valuable traits in emergency situations. Actionable does not equate to pressure-inducing environments.
Time series data is layered under requests of the user to allow more control.
Constellation provides instantaneous information on how long an anomaly has persisted over time and where these anomalies are located in, with an interactive deep-dive to match up data with anomaly actions.
Problem
Technical : Deciphering and managing dynamic, complex data.
Human : Providing tools to disperse information to multiple stakeholders throughout various stages of the cybersecurity analysis process.
Ideation
To develop an operating system that merges anomaly detection algorithms and data visualization.
Design Research
Our team sought various methods of design research, utilizing HCI methodologies:
analogous domains (ie. patient monitoring)
academic papers on current cybersecurity visualization systems
interviews with ground system analysts
We discovered that patient monitoring systems and cybersecurity health maintained similarities. System health became a metaphor for patients, and administration in relation to doctors. By studying patient monitoring systems, we defined actionable items: the elements of design called upon doctors to run to patients. These systems rely heavily on color, did not occlude raw data, and maintained labelling.
From literature reviews, the main issues for current cybersecurity visualization systems are: more work on tracking troubleshooting steps (1)(4), the ability to co-locate information for unencumbered comparison (2)(4), the need to illustrate explicit comparison information changes (3).
Interviews with stakeholders and users of current cybersecurity protocol illustrated how the responsibilities shift throughout the team.
Sketches
Prototypes
Solution
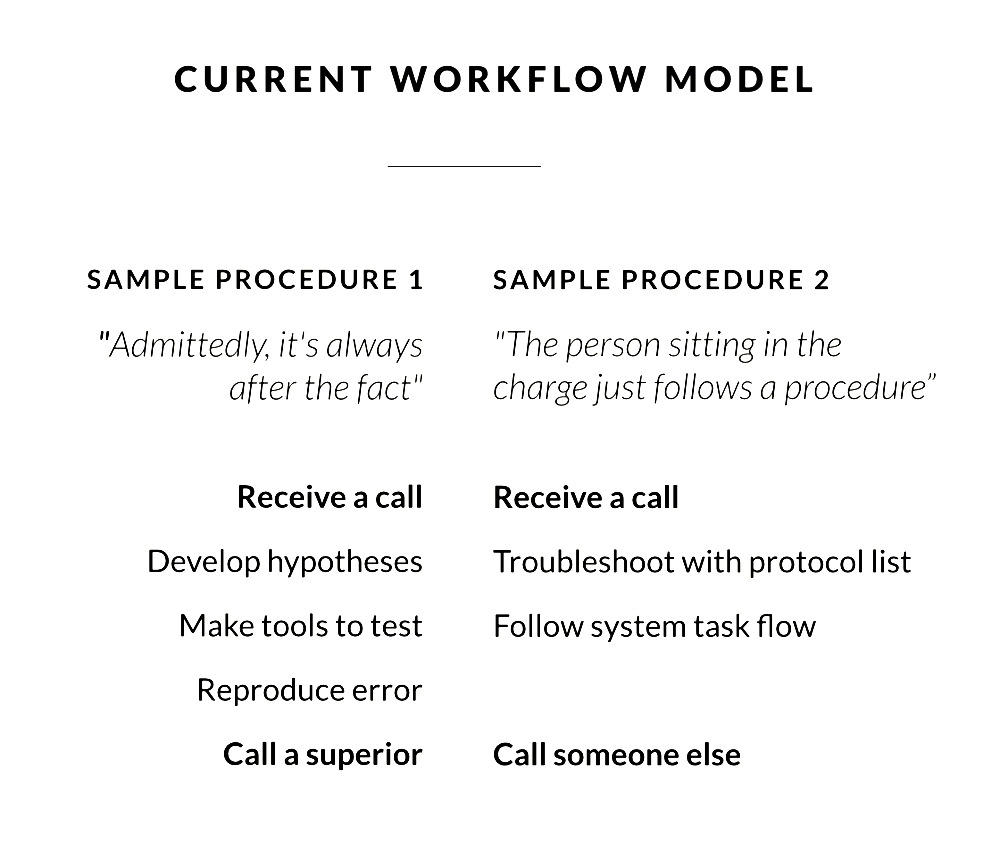
We built a new workflow model that highlighted situational awareness.
Bibliography :
1) NASA Preferred Reliability Practices; No. PD-ED-1255
2) Toward a Theory of Situation Awareness in Dynamic Systems Mica R. Endsley
3) Change Blindness: Why People Don’t See What Designers Expect Them To See Kathryn Whitenton
4) Visualizing Cyber Security: Usable Workspaces Glenn A. Fink, Christopher L. North, Alex Endert, and Stuart Rose
Tags: #ux #dataviz #designresearch